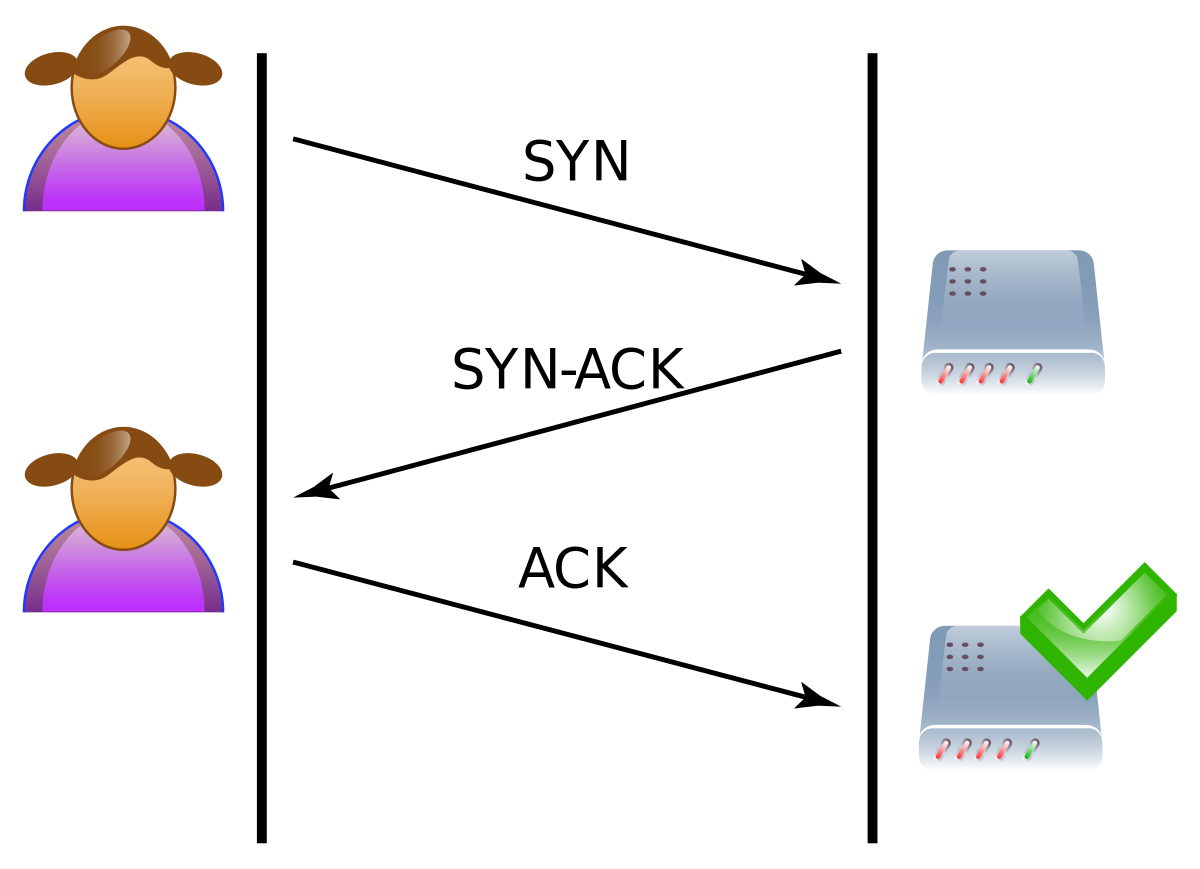
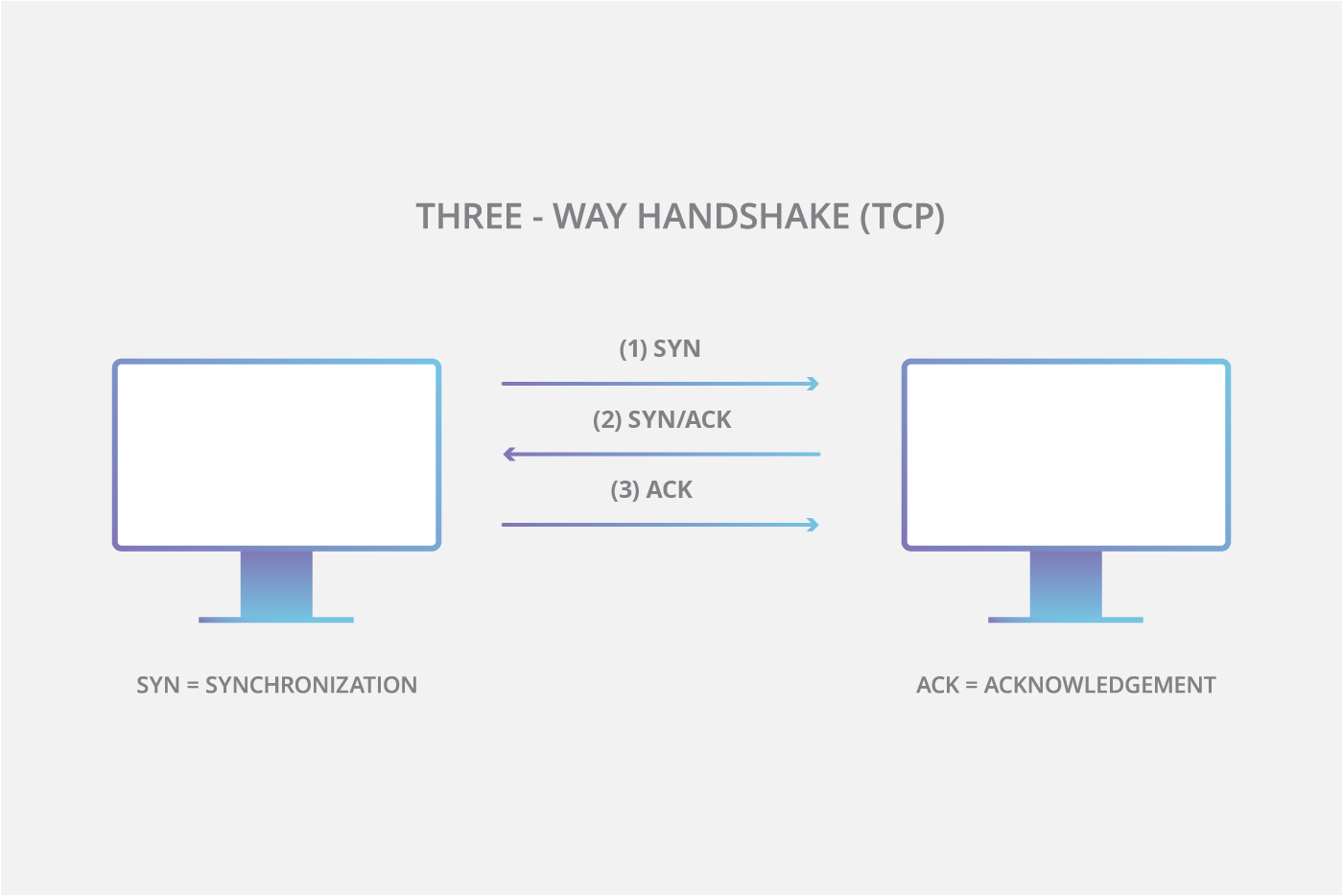
Client requests connection by sending SYN synchronize message to the server. Micro blocks —administrators can allocate a micro-record as few as 16 bytes in the server memory for each incoming SYN request instead of a complete connection object. Some systems may also malfunction or crash when other operating system functions are starved of resources in this way. If this is received, the server knows the request is legitimate, logs the client, and accepts subsequent incoming connections from it. Retrieved from " https: This should result in the client generating an RST packet, which tells the server something is wrong. 
| Uploader: | Dout |
| Date Added: | 25 June 2005 |
| File Size: | 5.32 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 73740 |
| Price: | Free* [*Free Regsitration Required] |
Please help improve this article by adding citations to reliable sources. By removing our filter and opening the protocol hierarchy statisticswe can also see that there has been an unusually high volume of TCP packets:.
Articles needing additional references from January All articles needing additional references Pages using RFC magic links. With the combined capacity of its global network, Incapsula can cost-effectively exceed attacker resources, rendering the DDoS attack ineffective. The server verifies the ACK, and only then allocates memory for the connection.
Retrieved 18 September During this time, the server cannot close down floodee connection by sending an RST packet, and the connection stays open. Retrieved from " https: At that point, the server cannot connect to any clients, whether legitimate or otherwise. This page was last edited on 18 Septemberat The server will wait for the acknowledgement for some time, as simple network congestion could also be the cause of the missing ACK.
TCP SYN Flood
Before the connection can time out, another SYN packet will floder. Micro blocks —administrators can allocate a micro-record as few as 16 bytes in the server memory for each incoming SYN request instead of a complete connection object. In this state, the target struggles to handle traffic which in turn will increase CPU usage and memory consumption ultimately leading to the exhaustion of its resources CPU and RAM.
From Wikipedia, the free encyclopedia.
DDoS Glossary
Wireshark is a little more involved than enterprise-grade software like Colasoft Capsa. Unsourced material may be challenged and removed.
However, in an attack, the half-open connections created by the malicious client bind resources on the server and may eventually exceed the resources available on the server. When a client attempts to connect to a server fflooder the TCP protocol e. Client responds with an ACK acknowledge message, and the connection is established.
Deal with bandwidth spikes Free Download.
Read our TCP Overview article for more information on the 3-way handshake. The connection is therefore established and data can be transferred between them. Client requests connection by sending SYN synchronize message to the server. Normally when a client attempts to start a TCP connection to a server, the client and server exchange a series of messages which normally runs like this:. Though the structure is insecure compared to many floodsr networks, an attacker could likely perform similar attacks after some sniffing.
Straight away, though, admins should be able to note the start of the attack by a huge flood of TCP traffic. At this point the server will no longer be able to serve legitimate client requests and ultimately lead to a Denial-of-Service.
How to Perform TCP SYN Flood DoS Attack & Detect it with Wireshark - Kali Linux hping3
A SYN flood is a form of denial-of-service attack in which an attacker sends a succession of SYN requests to a target's system in an attempt to consume enough server resources to make the system unresponsive shn legitimate traffic.
While modern operating systems are better equipped to manage resources, which makes it more difficult to overflow connection tables, servers are still vulnerable to SYN flood attacks. Alternatively Linux users can install hping3 in their existing Linux distribution using the command:.
By using this site, you agree to the Terms of Use and Privacy Policy. However, it has the advantage of being completely free, open-source, and available on many platforms. This enables transparent DDoS mitigation, wtih no downtime, latency of any other business disruptions.
If this is received, the server knows the request is legitimate, logs the client, and accepts subsequent incoming connections from it.
All of these metrics point to a SYN flood attack with little room for interpretation. In our lab environment, we used a Kali Linux laptop to target a Windows 10 desktop via a network switch.

No comments:
Post a Comment